Generate key pair under Windows
PuTTY's own key format .ppk is generated with the software PuTTYgen. After downloading and installing, we open PuTTYgen:
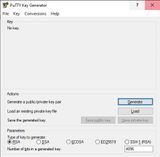
With PuTTYgen we create a private key and save it under private-key.ppk. It makes sense to export this key into the OpenSSH format to be able to establish a key-based connection with other software later on. With the private key we generate a matching public key, which we then transfer to the server.
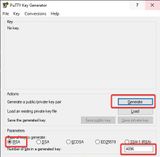
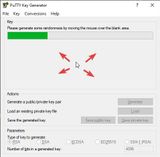
We set the parameters to RSA and the bit depth to 4096. To generate just click on Generate. In the empty gray area, the mouse pointer must be moved back and forth. These arbitrary movements are included in the calculation of the key. The progress bar informs about how long the movements have to be executed. The higher the bit depth, i.e. the complexity, the longer it takes. After the key is temporarily created, we enter a passphrase, which additionally AES-CBC encrypts the key.
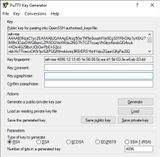
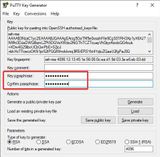
We save the public key with Save public key. The file extension can be for example .txt. We will store the content of this file later on our server.
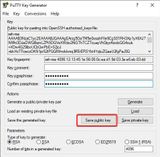
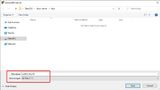
Similar procedure for the private key. This time we click Save private key and do not assign a file extension. The file extension .ppk is assigned automatically.
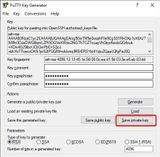
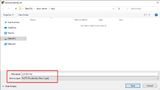
The private key in OpenSSH format is still missing. For this we open the menu Conversions and export with Export OpenSSH key. We save this file as private-key without file extension.
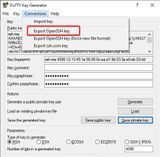
Before you close PuTTYgen, you should copy the key from the upper field. In this form, starting with "ssh-rsa" and all in one line, it is readable for the SSH service. We will copy this key to the server in a moment.
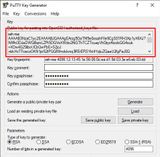
If necessary, we can also reconstruct it with the saved public key. The RSA key looks like this in my case:
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAtX9gXr8jJm5p6sqSGelcGjV0oov5OsTH2cGkYNfArq+jnhswBG52GsOSDy05EJjcGOeSuo4rr+vp/iUpl9Q3H/45k3T8AcLmnSZwzhWoxOs2mE9Esyrv6Ki4us4WJr2F8m7BbE5sym5kDOmUqSr1upT5THzccFDfNmtr9tQtYDls720/QcZ3SUk0ZDJTsyyHpe3vDUq4qcXgzKXpBhk58wsFcbKyeV+kAG8kzcdKPapmhswmP5KgtsHsGHwBZoyAS9nmDPSkxRmn18UgZjEY+wwBdGmcyTKwaphMcB6Ja+Tpu8iZLxjPATdqTmIO0AVEhDw7pCuO/9yoQf2WKkUdiQ==
Done! Our key pair is now in different file formats on our computer. You should not lose the private key and the passphrase, because without the key you (and nobody else) will not be able to access the server later after the changeover.
Store public key on the server
We have to write the content of the public key file in the user directory of tom under Home into the file ~/.ssh/authorized_keys. To make sure you are logged in with the right user, you can check this with whoami:
__$ whoami
It is quite possible that the file does not exist yet. Therefore, we first create the ~/.ssh folder with mkdir:
__$ mkdir ~/.ssh
After that we create the file ~/.ssh/authorized_keys with nano and can enter the content of the public key at the same time:
__$ nano ~/.ssh/authorized_keys
And paste the key with the right mouse button. Just save and you're done. (CTRL+s, CTRL+x).
~/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAtX9gXr8jJm5p6sqSGelcGjV0oov5OsTH2cGkYNfArq+jnhswBG52GsOSDy05EJjcGOeSuo4rr+vp/iUpl9Q3H/45k3T8AcLmnSZwzhWoxOs2mE9Esyrv6Ki4us4WJr2F8m7BbE5sym5kDOmUqSr1upT5THzccFDfNmtr9tQtYDls720/QcZ3SUk0ZDJTsyyHpe3vDUq4qcXgzKXpBhk58wsFcbKyeV+kAG8kzcdKPapmhswmP5KgtsHsGHwBZoyAS9nmDPSkxRmn18UgZjEY+wwBdGmcyTKwaphMcB6Ja+Tpu8iZLxjPATdqTmIO0AVEhDw7pCuO/9yoQf2WKkUdiQ==
CTRL+x to close, type y to save
EnterTo be really sure if the public key has been saved, we check with less:
__$ less ~/.ssh/authorized_keys
The output should look something like this:
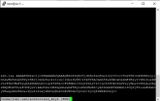
authorized_keys (quit with q)The public key is now stored on the server, which is wonderful, but doesn't do us any good yet. We still need to change the SSH authentication method. We will do that in the next chapter: Change authentication method.